
Gilberts Cyber Virtual Chief Information Security Officer (vCISO) services provide organizations with on-demand access to experienced cybersecurity leadership, without the need to employ a full-time in-house CISO, across these areas of expertise.
Our service includes our vCISO Platform that is available to our clients 24x7x365 that displays current status and forward progress in maximizing the effectiveness of our client’s cybersecurity program.
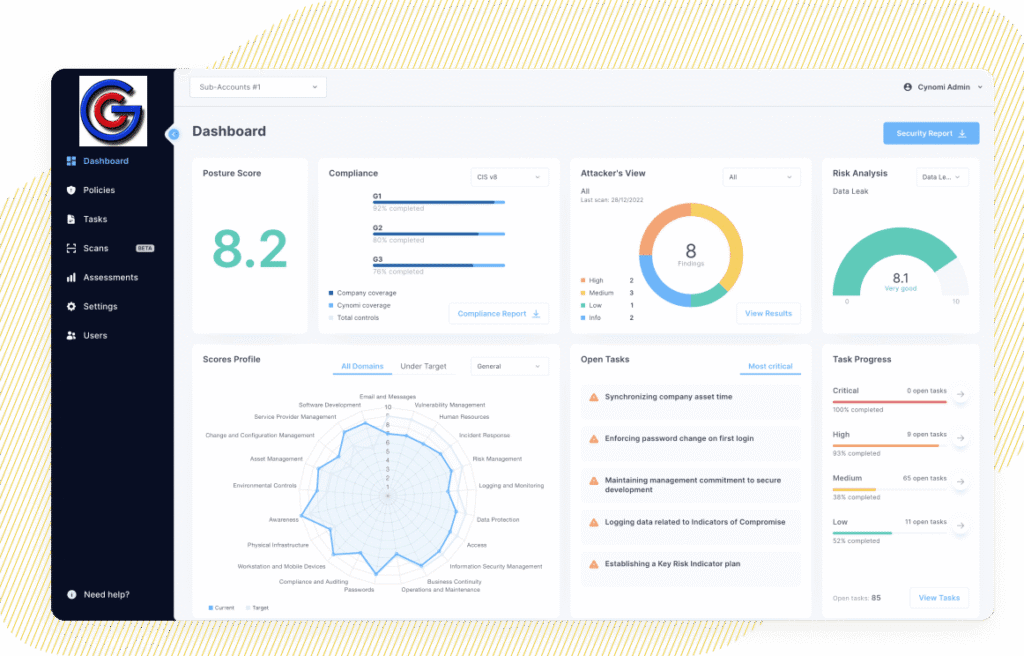
vCISO Platform Features:
| External Scanning |
| Our vCISO Platform scans Internet Protocol (IP) Addresses and and Uniform Resource Locators (URLs) to discover vulnerabilities and secured configurations. This includes scanning risky ports, checking protocols and encryption, verifying email configuration parameters, technology updates of web applications and more. Scan results are available within a few minutes and are readily accessible for client users to drill down into each scan finding to see an in-depth description and remediation options. Detected vulnerabilities are automatically added to the a task list ranked by severity. |
| Internal Scanning |
| Internal scanning discovers client assets like active directory and endpoints and assess its security hygiene and configuration. |
| Upload Scan Files |
| Clients can upload client performed scan data such as NESSUS scan data, Qualys scan data, or Microsoft Secure Score CSV files. Scan findings are aggregated in an aggregated table and linked to relevant tasks and policies. |
| Security Assessment |
| Our vCISO Platform continuously parses our clients’ network and asset profile against industry-specific security standards, regulatory frameworks, industry-specific threat intelligence, and information from the security questionnaires and scans results. Based on our clients’ specific profile, relevant cyber domains are dynamically picked and matched with the optimized cybersecurity requirements that further maximization of the client’s cybersecurity program. Each requirement is assigned a criticality level that represents the importance of specific requirements to improve our client’s security posture. For example, cyber risks such as ransomware and data leaks are calculated based on our client’s sensitivity of risk associated with those types of attacks. The result is a single pane of glass view of our client’s overall security posture and its progress over time that includes (1) Overall security posture score, (2) Vulnerability and exploit gap analysis, (3) Risk score across specific threat vectors, (4) Remediation plan with actionable prioritized tasks, and (5) Status against various compliance frameworks requirements. |
| Comprehensive, Continuous Compliance Assessment |
| Our vCISO Platform helps our clients meet their specific compliance requirements by presenting our client’s current compliance status against cybersecurity frameworks such as CIS v8, ISO 27001, NIST CSF 1.1, NIST CSF2.0, NIST-171, NIST-SSDF, SOC 2, CMMC L1, CMMC L2, GDPR, NIS2, PCI-DSS, HIPAA Security, Cyber Essentials, FTC Safeguard Rule, SEC compliance, ICS Cyber Security, CCPA, FFIEC. Our compliance module is updated continuously and presents the details of each security control in each framework and tracks how each task maps to each framework so our clients are continuously aware of their compliance level. Our clients can also download a dedicated compliance status report includes the following catagories: (1) Overall compliance status, (2) List of controls, (3) Maturity level, (4) Control status, (5) Control mapping to framework, (6) Implementation status, and (7) Hyperlink to the relevant tasks. With this information, our clients can easily understand where our clients stand with respect to their compliance level and what gaps must be closed to comply with applicable frameworks. Remediation plans for each framework are available and can be selected with just a few mouse clicks. |
| Customized Security Policies |
| Our vCISO Platform automatically generates a set of security policies specific to our client’s requirements. Policies are custom-created, crafted to be easy to follow, actionable, and leverage decades of built-in CISO expertise. In the Policies view of the platform, the following information is presented: (1) Score for all generated policies, (2) Option to drill down into the details of each policy including purpose, scope and protection requirements, (3) Information on the tasks and progress to be completed to secure the policy’s domain. For example, the Policies view shows our client’s score per policy and allows our clients to drill down to see a breakdown of each policy’s specific requirements. |
| Actionable, Prioritized Remediation Tasks |
| Actionable remediation tasks are created for each policy requirement that are intuitive, easy and to understand and follow. Remediation tasks are displayed in an AI-generated prioritized list that includes its severity and status types that include the following: (1) Technical controls, (2) Administrative procedures, (3) and Security components configurations. Each task can be drilled into for step-by-step guidance to implement a control. Tasks are also customizable, allowing you to . Lists and tasks are editable and allow our clients to add best practice guidance, evidence that supports the task, and the ability to postpone or defer certain tasks without affecting policy status or severity. Our clients can apply filters, jump back to tasks that are already in progress, and focus on high severity tasks. All progress is tracked in the vCISO Platform. All tasks completed are automatically reflected in the client’s overall security posture score. |
| Plan and Roadmap |
| Our vCISO Platform leverages AI to create suggested plans and provides our clients with tools to (1) Plan, (2) Optimize task management, (3) Track task progress, (4) Manage optimization, (5) Assign tasks to short, medium, and long-term plans, (6) Allocate tasks to plans, (7) Add task due dates, (8) Filter tasks according to framework, due date, and status, (9) Edit tasks to adjust for changing needs, (10) Add information and evidence to each task with specification, details, and recommendations, and (11) Add product and service recommendations to tasks for upselling new services. |
| Reports |
| Our vCISO Platform allows our clients to generate reports that include our client’s security level, improvement, trends, compliance gaps and comparisons with industry benchmarks. Standard reports include the following: Full Report: The Full Report presents our client’s cybersecurity posture and our suggested remediation plan. Over time, updating the Full Report will reflect our work with our client to work together to maximize the effective ness of our clint’s cybersecurity program, achieve security improvements we will work together . Risk Findings Report: The Risk Findings Report presents Our clients’ risk exposure based on the platform scans. Compliance Report: The Compliance Report presents our clients’ compliance readiness and status. The reports above (1) present an accurate current snapshot of our client’s current cyber posture status, (2) track progress we have helped our clients achieve to maximizing the effectiveness of our client’s cybersecurity program, and (3) facilitate conversations with management and and client stakeholders by clearly presenting security risks with explanations that help stakeholders understand cybersecurity requirements. |
| Continuous Optimization |
| Our vCISO Platform continuously updates our client’s risk score, compliance readiness policies, task status, and progress over time as we work together to maximize the effectiveness of our client’s cybersecurity program. |
Our vCISO Platform provides a visual tool to track progress across our Areas of Expertise:
| Asset Security – Addresses the physical requirements of information security. |
| Communication & Network Security – Covers the design and protection of networks. |
| Compliance – The practice of following laws and regulations to protect a business’s digital information from cyber threats. |
| Data Security & Privacy – Protects data from unauthorized access, use, disclosure, disruption, modification, or destruction, while also ensuring compliance with privacy regulations. |
| Governance, Risk & Compliance (GRC) – The comprehensive framework that helps organizations manage their IT strategy by aligning it with business objectives, addressing potential risks, and ensuring adherence to relevant industry regulations and laws. |
| Identity & Access Management (IAM) – The first line of defense for protecting information assets. |
| Incident Management – The process of identifying, analyzing, and responding to security threats. |
| Physical Security – A crucial yet often overlooked aspect of cybersecurity. It involves protecting the hardware, software, networks, and data from physical actions or events that could lead to data breaches, system failures, or unauthorized access. |
| Risk Response & Reporting – The process of identifying potential cyber threats, assessing their likelihood and impact, deciding on appropriate actions to mitigate those risks (response), and then communicating the findings and actions taken through detailed reports to relevant stakeholders within an organization, including management and boards, to ensure informed decision-making about cybersecurity posture. |
| Secure Access Service Edge (SASE) – A cloud-delivered architecture, defined by Gartner, that provides secure network access to cloud applications through a common “SASE” framework. |
| Security Architecture & Engineering – The tools, systems, and processes necessary to carry out effective cybersecurity capabilities. |
| Security Assessment & Testing – The design, performance and analysis of security testing. |
| Security Governance – The creation and management of a set of policies, processes, and practices that help organizations manage their digital assets and information systems. |
| Security Operations – Integrates information security management principles into the day-to-day running of IT functions to support business objectives. |
| Security Program & Policy Management – The practice of managing an organization’s overall cybersecurity strategy through the strategic process of developing, implementing, and overseeing an organization’s cybersecurity policies, procedures, and practices to protect its sensitive information systems, networks, and data from cyber threats, including defining clear guidelines for user access, data handling, incident response, and risk mitigation, while also regularly reviewing and updating these policies to maintain effective security measures. |
| Security Risk Management – Examines the complexities of classifying information and helps clients appreciate how information security functions. |
| Software Development Security – The processes and practices involved in developing secure software systems that are resistant to malicious attacks and unintended vulnerabilities. |
| Threat Analysis – The practice of actively identifying and analyzing potential cyber attacks to proactively protect against them by establishing a process in which potential cyber threats that could harm an organization’s systems, networks, or data are identified, assessed, and understood, using a combination of data analysis, security intelligence, and forensics to evaluate and prioritize the potential risks involved. |
| Threat Intelligence – The process of collecting, analyzing, and applying information about current and potential cyber threats to an organization’s cybersecurity program to enhance the organization’s cybersecurity posture. Threat intelligence involves gathering data from various sources, identifying patterns, and using this knowledge to prevent or mitigate cyberattacks. |
Call (541) 508-5574
Copyright 2025 Gilberts Cyber. All rights reserved.
1900 NE Third Street, Suite 106 #1088, Bend, OR 97701

A USMC Veteran-Owned Business
